What is Aloha?
Aloha means “Hello”. It is a multiple access protocol in a data link layer and explain how multiple terminals/station access the medium or channel without any collision or interference. The basic idea is to use different frequencies in a hub/star configuration.

- The hub broadcast data packet to every client at the outbound channel.
- The Client broadcast data packet to Hub at the inbound channel.
- If the hub receive data packet correctly a short acknowledgement is sent to the client from the hub.
- If the client does not receive any acknowledgement in the meantime it assume that the hub did not received the packet and again retransmit the same data packet at a randomly selected time interval.
- This mechanism is used to avoid any collision when two terminals communicate simultaneously.
There are two types of Aloha
- Pure Aloha
- Slotted Aloha
- In pure ALOHA,Whenever station is ready they are allowed to send.
- When two or more stations transmit frames simultaneously, collision occurs and the frames are destroyed.
- In pure ALOHA, whenever the station transmits a frame, it expects the acknowledgement from the receiver end.
- If acknowledgement is not received within specified interval of time, the station assumes that the frame (or acknowledgement) has been destroyed.
- If the frame is destroyed because of collision the station waits for a random amount of time and retransmit the same frame again. This waiting time must be random otherwise the frames will collide again and again.
- A central clock/station will inform all the other stations about the start of each slot.
- Therefore, pure ALOHA explains that whenever there is collision, each station must wait for a random amount of time before retransmitting its frame. This randomness will help avoid more collisions.
Slotted Aloha
- Slotted ALOHA was invented to improve the efficiency of pure ALOHA as chances of collision is still there because the random amount of time for which they wait before sending the frame may be same in pure ALOHA.
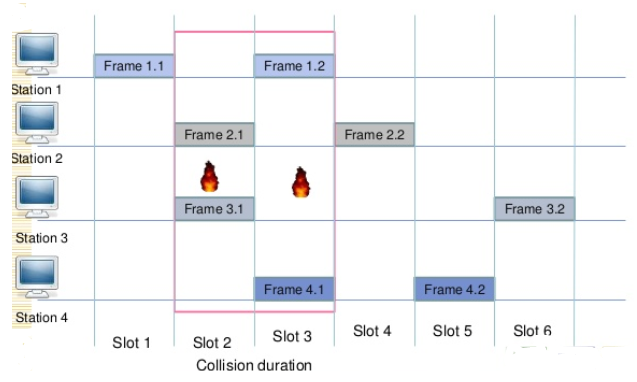
- In slotted ALOHA, the time of the shared channel/medium is divided into discrete intervals called slots.
- The stations can send a frame at the beginning of the slot only and one frame can be sent in each slot.
- In slotted ALOHA, if the station misses the beginning of a slot it has to wait until the beginning of the next time slot for sending the frame.
- In slotted ALOHA, there is still a possibility of collision if two stations try to send the frame at the beginning of the same time slot.
- Slotted ALOHA is still better than the Pure ALOHA as chances of collision are reduced to one-half.

Comments
Post a Comment
Please do not post any spam link in comment box